Introduction of Emerging Cyber Security Attacks and Threats
The term “Emerging Cyber Security Attacks and Threats” describes the methods that malicious actors are using to compromise, interact with, or harm data, networks, and information systems. As technology develops, they might include complex malware, ransomware, phishing scams, zero-day exploits, and other advanced persistent threats that pose serious hazards to both individuals and companies.
Cybercriminals are always developing new methods to steal personal information and cause havoc in the online world in order to keep up with the rapid pace of technological advancement. In order to shield yourself against these cyber security attacks and threats, you will need to be current on the most recent developments in new attacks and implement preventive measures to lock down your systems and data.
Here are some of the most concerning emerging cyber security attacks and threats:
- Fraudsters are leveraging artificial intelligence and machine learning to conduct increasingly complex and nuanced assaults. Attacks fueled by AI, for instance, may employ natural language processing to send phishing emails that are both effective and difficult to spot. Cyberattacks driven by artificial intelligence (AI) are attacks that use machine learning and other AI-powered techniques to carry out their malevolent objectives. As the technology used in these assaults improves, they become harder to detect and more complex. Artificial intelligence algorithms may be used to improve the effectiveness of phishing emails by making them seem more legitimate and tailored to the individual. The use of AI algorithms enables cyber security attacks and threats to narrow their attention to the most susceptible people and organisations by scanning massive volumes of data for indicators of compromise.
 Even more, assaults backed by AI may automate several steps of the attack process, making it easier for hackers to launch widespread operations with pinpoint accuracy. As a result, the damage caused by such assaults may be far more severe than that caused by standard cyberattacks. Organizations need to be aware of the dangers presented by AI-powered cyberattacks and take measures to safeguard their systems and data in light of the widespread use of AI and ML in both the public and private sectors, explaining you below in 4 points.
Even more, assaults backed by AI may automate several steps of the attack process, making it easier for hackers to launch widespread operations with pinpoint accuracy. As a result, the damage caused by such assaults may be far more severe than that caused by standard cyberattacks. Organizations need to be aware of the dangers presented by AI-powered cyberattacks and take measures to safeguard their systems and data in light of the widespread use of AI and ML in both the public and private sectors, explaining you below in 4 points.-
- IoT Hardware: There is a new security risk due to the proliferation of IoT devices in people’s homes and workplaces. Several such gadgets have inadequate safety features, making them inviting targets for online fraudsters. Certain Internet of Things gadgets, for instance, may send sensitive information without even the most basic encryption protections, or they may ship with default passwords that are easy to guess or locate online. If a hacker compromises one IoT device, they will have a foothold in the network from which to launch more attacks. As a result, they could be able to steal private data, plant malicious software, or even seize complete control of the device for use in other assaults. The low processing power and memory of many IoT devices also makes it difficult to install security software or upgrade the firmware to address cyber security attacks and threats flaws.
This implies it may be difficult or impossible to fix the device after a vulnerability has been detected, leaving it open to attack. Following cyber security attacks and threats best practises is essential for protecting against the cyber danger presented by IoT devices. Protecting data in transit against unauthorised access involves measures such as adopting strong passwords, keeping firmware up-to-date, and encrypting data at rest. Furthermore, companies should think about using security technologies like firewalls and intrusion detection systems to safeguard their networks from malicious infiltration.
- Malicious Ransomware: Cybercriminals are becoming more and more ingenious in their attempts to encrypt data and demand money in return for the decryption key, which has led to an increase in the frequency and sophistication of ransomware assaults. There have been reports of attackers threatening to leak private information unless they get a ransom. During the last several years, ransomware attacks have grown more targeted, with cybercriminals going after the businesses and organizations they think are most likely to pay up. In 2024, hackers will likely use even more advanced methods, and this trend is expected to continue. Also, ransomware attackers now have more entry points due to the rising use of cloud computing and other forms of remote work. Ransomware attacks that take advantage of flaws in cloud systems or the devices that access them might become more common as more organisations shift their data and systems to the cloud.
Businesses may better defend themselves against ransomware attacks by adhering to cybersecurity best practises such as regularly backing up data, updating software and systems, and deploying anti-malware software to identify and stop assaults. Companies also need to train their staff to spot and prevent phishing schemes and other methods ransomware perpetrators try to get access to sensitive information.
- Cloud Security- Concerns about the safety of cloud-based systems are on the rise as more and more organisations migrate their data and applications there. To ensure the safety of their cloud infrastructure, cloud service providers and their customers must work together, but customers must also take precautions to protect their own data and applications. An rising number of people are turning to cloud services, but this influx of users has also led to an increase in cybercrime. Here are some of the main cloud security threats to watch out for in 2023:
-
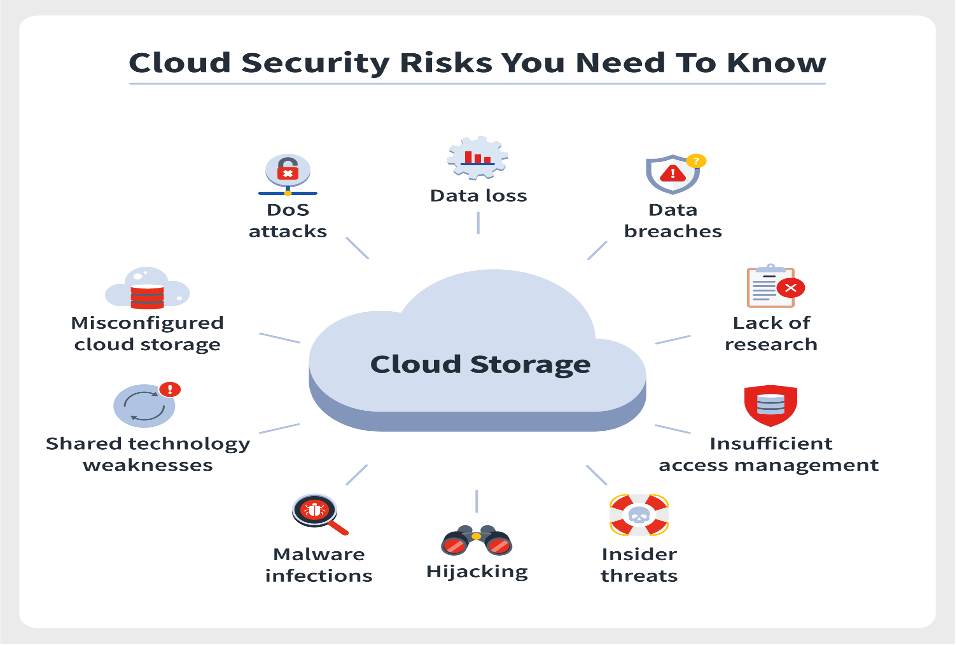
- Data breaches: Without adequate protections in place, sensitive information stored in the cloud is at risk of being stolen. The loss or disclosure of sensitive data may lead to monetary and reputational consequences for the affected organisation. With so much sensitive information potentially accessible to cloud service providers and their staff, insiders pose a significant risk. Data security is another concern for businesses that store their information in the cloud since workers might leak it on purpose or by mistake.
- Malicious attacks: Hackers and cybercriminals are actively seeking out cloud systems to exploit weaknesses in and steal sensitive information from. Phishing schemes, malware, and ransomware are all examples of such assaults.
- Incorrectly configured cloud services: Sensitive information stored in the cloud may be at risk if cloud services are not properly setup. Incorrect actions taken either by the company using the cloud services or the cloud service provider might lead to this.
- Downtime and service interruptions: Hardware problems, software issues, and natural catastrophes are just some of the many potential reasons of downtime and service disruptions for cloud services. Companies relying on the cloud might see a drop in income and productivity as a consequence.
Regular cyber security attacks and threats audits, access limits, and encryption of critical data are only some of the best practices for cloud security that businesses may employ to defend themselves from these dangers. Furthermore, businesses should consult with their cloud providers to learn about the security options available and the best way to safeguard their data in the cloud.
- Cryptojacking- This practice, known as “crypto jacking,” involves the illegal use of a victim’s computer to mine bitcoin. As the market value of cryptocurrencies rises, fraudsters are seeking more sophisticated methods to exploit weak points in computer networks.

Although while crypto jacking has been less common in recent years, it is still a major issue for businesses and people. Specifically, cryptojacking may be a major problem for businesses with a lot of connected devices, since such gadgets might be used to mine cryptocurrency, which could have a negative effect on the business’s productivity and resources.
Use of anti-malware software and maintaining software and system updates are two examples of solid cybersecurity practices that may help protect people and businesses against cryptojacking. In addition, businesses should keep an eye out for any anomalous network behavior, such as a spike in CPU utilization or traffic, since these might be signs of a crypto jacking assault, cyber security attacks and threats.

Implementing cyber security attacks and threats best practises is very necessary in order to protect against not just these but also other newly emerging cyber threats. Use of difficult passwords, regular software upgrades, and two-factor authentication are all recommended for further security. Using security software such as firewalls, antivirus and antispam solutions, and intrusion detection systems may provide businesses with additional protection against attacks and the ability to spot them at an early stage.
Last but not least, it is of the utmost importance to be current with the most recent attacks and dangers in the field of cyber security attacks and threats. The risk environment is continually shifting; therefore, it is essential to remain vigilant. You may help protect your firm from the harm that can be caused by the new types of cybercrime that are emerging by adopting preemptive measures to protect the security of your systems and data
Conclusion
In conclusion, the landscape of cyber security is constantly evolving, with emerging threats and sophisticated attacks posing significant challenges to individuals, businesses, and governments alike. The rise of advanced persistent threats (APTs), ransomware, phishing schemes, and the exploitation of vulnerabilities in Internet of Things (IoT) devices highlights the need for robust and adaptive security measures. The increasing frequency and complexity of these attacks underscore the importance of continuous monitoring, regular updates, and comprehensive security protocols.
Additionally, fostering a culture of security awareness among employees and stakeholders is crucial in mitigating risks associated with human error. By combining technological advancements, strategic policies, and educational initiatives, we can enhance our defenses and protect critical infrastructure, sensitive data, and the overall integrity of our digital ecosystem.
also check this out for more: Emerging Cyber Security Attacks and Threats